Technology is everywhere. In our homes, in our pockets, in our businesses. Digitalization has made the world a smaller place and the benefits that new technology brings are enormous. But, as a modern “classic” saying goes, “with great power, comes great responsibility”. As technology adoption is on the rise, so are cybersecurity threats, such as the more recent botnet attacks.
Want to know which ones they are?
Read on and find out more.
What Is a Botnet Attack?
Before speaking about the recent botnet attacks, let’s have a look at what a botnet and a botnet actually attack are. The word botnet is derived from “robot network”. A botnet represents a large group of malware-infected devices controlled by a single operator. These devices are connected to the internet – and it is via the internet that botnet attacks happen.
These compromised devices are used by cybercriminals to launch attacks that disrupt services and gain unauthorized access to other systems. A botnet attack is a large-scale cybersecurity attack carried out by these devices, which are controlled remotely.
Traditionally, malware replicates itself on a single device or system – infecting one device at a time. Botnets, on the other hand, owe their strength to their large numbers. With botnet attacks, the botnet controller can perform several actions, on several devices, at the same time. This makes botnet attacks more difficult to stop.
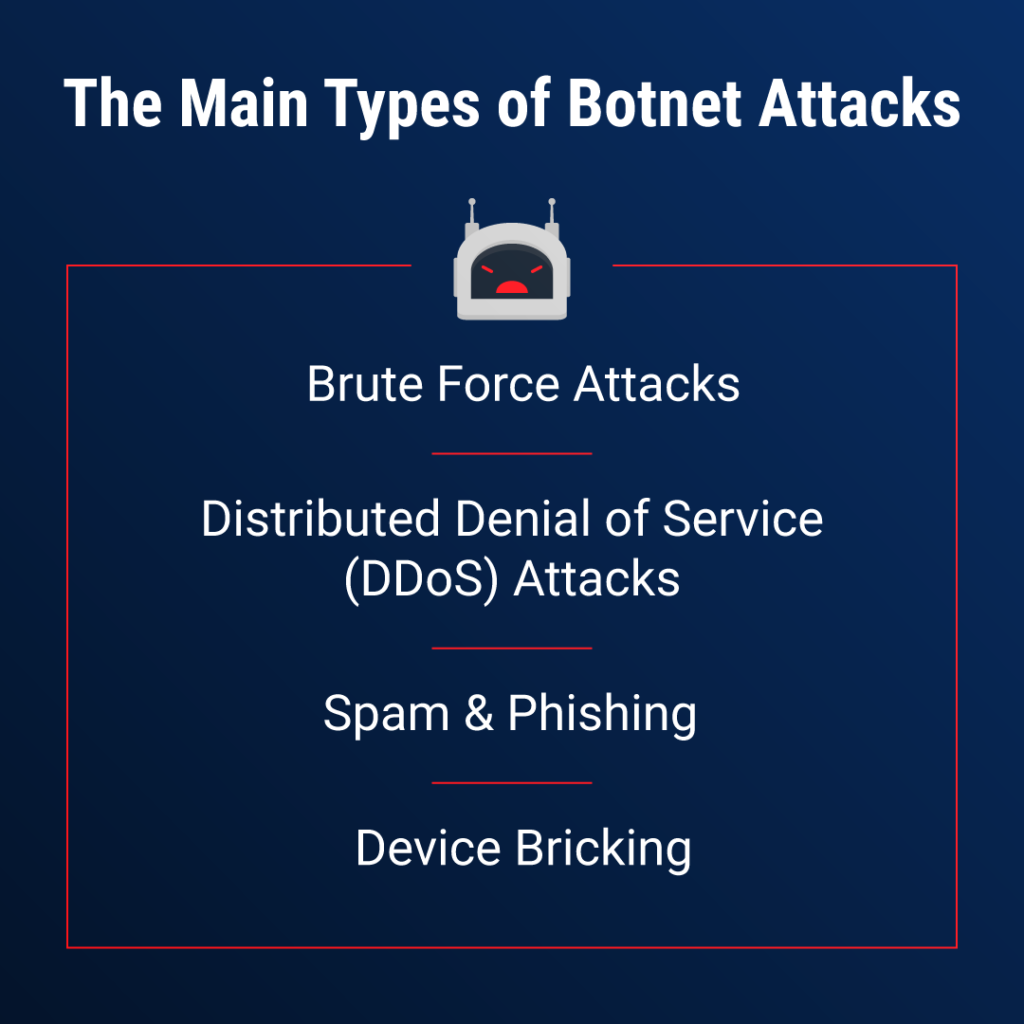
4 Types of Botnet Attacks
The world of cybersecurity is rarely simple and straightforward and we know it can be daunting to the untrained. As there are several types of malware out there, so are there several types of botnet attacks. And the complexity of these cyberattacks keeps increasing year after year.
Here are 4 types of recent botnet attacks:
Brute force attacks
As the name suggests, this is an “aggressive” kind of attack, used when the attackers don’t know any of the target’s passwords. This attack method uses rapid repetitive password guessing technology. The malware “attacks” the targeted system with multiple passwords attempts until the right one is found.
Distributed Denial of Service (DDoS) Attacks
A DDoS attack aims at disrupting the normal traffic of a server, service, or network. It does this by sending high amounts of internet traffic that overwhelms the target. On the one hand, this stops real traffic from reaching its destination; on the other hand, it can shut down the whole system.
There have been many recent botnet attacks using this method, which is quite efficient. DDoS attacks use compromised systems (computers or other networked systems like IoT devices) as sources of attack traffic.
Spam & phishing
These attacks involve using spam email with the ultimate goal of phishing confidential information or credentials. They are usually targeted at company employees, who are tricked into sharing login details or other sensitive data. When successful, phishing can help gain access to more devices and grow the botnet.
Device bricking
The term “bricking” is usually used to describe a device that is no longer usable, as it has been damaged beyond repair. Botnet attacks that aim at bricking devices usually happen in several phases. A device is first infected with malware that deletes its contents, which often also removes evidence of the attack. The end goal of a device bricking attack is to stop the device from working.
The Recent Botnet Attacks: Top Trends
According to Imperva’s 2021 Bad Bot Report, bad bot traffic amounted to 25.6% of website traffic in 2020. Less than 60% of traffic was human, while 15.2% of traffic was driven by good bots. If you are a marketer or business owner, you should be aware that at least part of the traffic you are receiving is driven by bots.
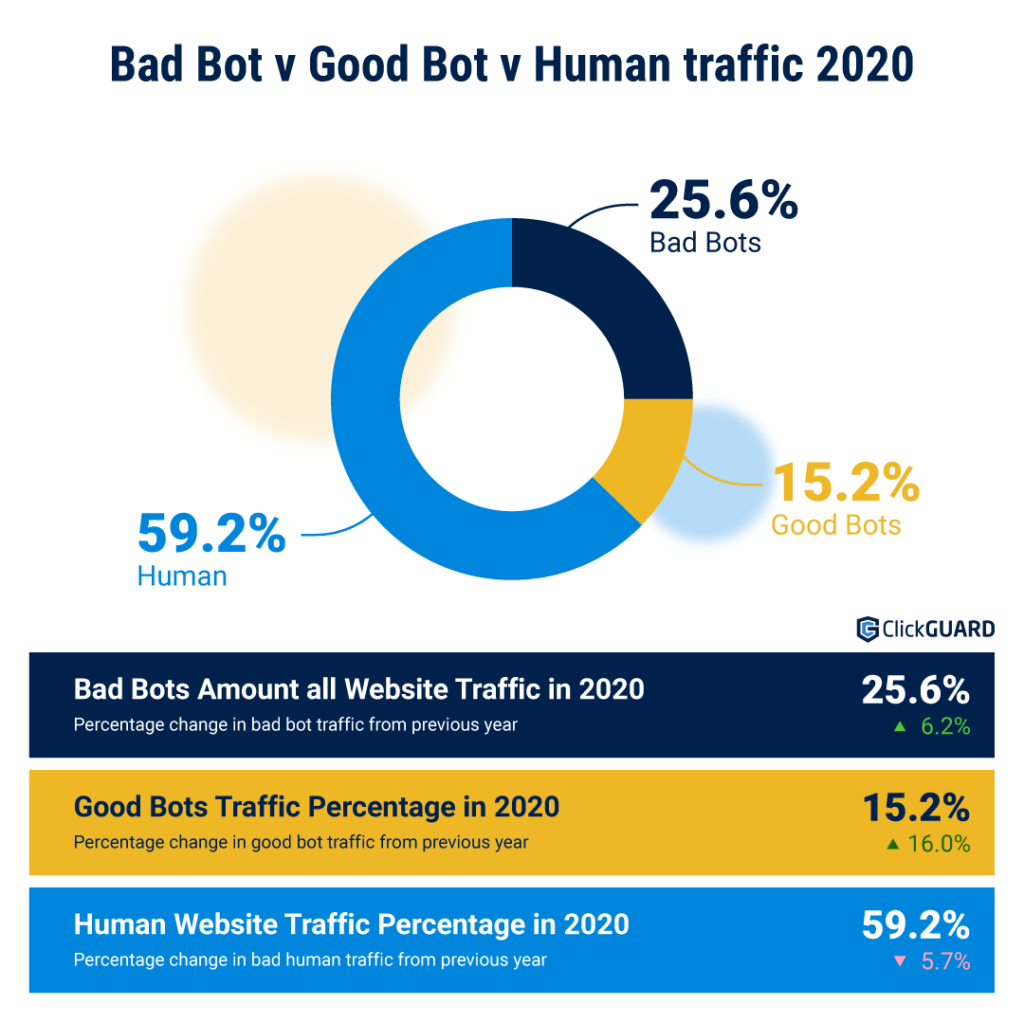
Data source: Imperva
The same report has also shown that:
- The industry most hit by bad bots is Telecom & ISPs, with 45.7% of this traffic, followed by Computing & IT at 41.1%; Sports, News, and Business Services have also been highly targeted.
- Moderate and sophisticated bots accounted for 57.1% of bad bot traffic, representing an obvious majority.
- Botnet attacks often target mobile devices – mobile clients accounted for 28.1% percent of bad bot requests.

The Recent Botnet Attacks of 2021
A report on cybercrime from LexisNexis Risk Solutions has shown that the number of botnet attacks has risen abruptly during the first half of 2021, the number growing by 41%. Another report by FortiGuard Labs shares that the percentage of organizations that have detected botnet activity has jumped from 35% to 51% around the same time.
Cybersecurity attacks seem to be getting more common and more complex. Some of these attacks have raised international concern and have reached the mainstream media. The recent botnet attacks of 2021 include several culprits, like:
Trickbot
The rise in recent botnet attacks in the first half of 2021 is partly attributed to the malware Trickbot making a “comeback”. This malware was supposedly taken offline in 2020, but it has been revived bearing new capabilities. It can now scan the UEFI/BIOS firmware of the targeted system for vulnerabilities, making it a powerful and adaptable threat.
Mirai
Mirai is another botnet threat that has risen in 2021. It is a kind of malware that was discovered back in 2016. Its source code has become freely available in 2016 and it is still an important threat in the digital landscape, as new variants keep appearing.
Its codebase has continued to be used for recent botnet attacks during 2021. Mirai mainly works by targeting IoT devices. It then creates a botnet that uses those devices and launches DDoS attacks against their final targets.
Gafgyt
This malware is quite similar to Mirai. It is also used to build a botnet and launch DDoS attacks against its targets. Gafgyt has been known since 2014 and, as in the case of Mirai, its source code has become public in 2015. Recent botnet attacks have been fueled by Gafgyt variants that attack IoT devices.
Meris
Meris has been behind some of the biggest DDoS attacks over the summer of 2021. A botnet consisting of an estimated 250,000 malware-infected devices has broken the record for the largest DDoS attack twice during 2021.
The attackers behind the Meris botnet have operated by sending emails to large companies and asking for a ransom payment. If the victims don’t pay, the botnet starts deploying small attacks on the victim’s system. The attacks gradually grow in size to put pressure on the targets.
How to Stay Safe from Botnet Attacks?
The best way to deal with cybersecurity attacks is to prevent them. Recovery from a botnet attack can de difficult and costly. Recent botnet attacks have shown that it’s better to prevent than to cure. Here are some tips on how to keep your system safe:
- Training and education: educate all employees and partners on the risks posed by botnet attacks in general, and phishing in particular.
- New devices: Only add new devices to your network once you’re sure they meet the security standards of your organization.
- Software updates: Make sure your system and device software are always up-to-date; regularly check for software updates.
- Credentials: Change login credentials for all your devices regularly.
- Limit access to your devices: make sure you monitor and restrict access to your organization’s devices; only relevant members of your organization should have access to your system or devices.
But what if you get attacked anyway? Even if you follow all of these steps and manage to keep your organization educated and your system up-to-date, malware is getting more and more sophisticated.
In case of a botnet attack, you should try and regain control over the infected device as soon as possible. You can either try to disable access to the central server (which works as the main resource for the botnet) or to cut off connections to control servers. Scan your system for malware and reinstall software; IoT devices may need a full factory reset to remove malware and to work again. If you are the victim of a botnet attack, you should focus on limiting the damage to your system.
The world of cybersecurity is a complex one and recent botnet attacks have proven that. We cannot expect the number of attacks to drop in 2022. To avoid being a victim, you should take precautionary measures: educate people, monitor and analyze your traffic and your devices, invest in tools that help you protect your assets.