In 2020, Google reported more than 2 million separate instances of website spoofing.
But surely you can tell the difference between a popular website and an internet scam?
Not always…and don’t call me Shirley.
Spoofing is definitely one of the most common types of cybercrime too. It comes in many shapes and sizes, but today we’re going to focus on website spoofing, and how it’s used to steal from PPC advertisers.
What Is Website Spoofing?
Also known as domain spoofing, cybercriminals set up a fake or ‘spoofed’ website, deliberately designed to imitate and steal traffic from a popular website that people know and trust. When visitors arrive there in error, they’re subjected to phishing attacks, malware, and identity theft.
Website spoofing is a major hazard for PPC advertisers, too – even if you’re vigilant about your PPC ad placements, it’s all too easy for your ads to end up on a spoofed site, and the ensuing click fraud can wipe out your ad budget in minutes.
A spoof website is a form of social engineering – an umbrella term used to describe all the ways cybercriminals can fool you into doing something stupid, like clicking a dodgy link or entering your details.
Modern browsers are built to defend against social engineering. The danger occurs when different forms of social engineering are combined – for example, email spoofing is used to direct you to a spoofed website, for a phishing attack.

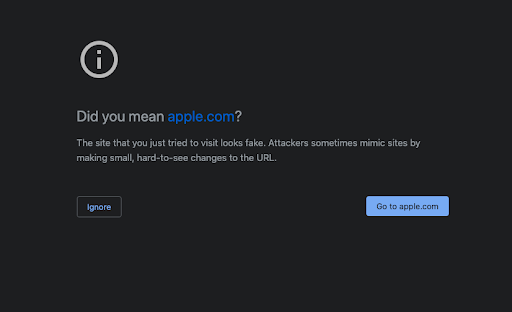
Each element in this chain can be used separately (and we’ll talk about the other elements shortly). However, it’s unlikely a visitor will land on a spoofed website without being directed there by an email or text. Your browser automatically detects the majority of these sites, and blocks them from search results. Even if you’ve followed a dodgy link, you’re likely to see a warning first, like this:
But for PPC advertisers, website spoofing represents a different kind of threat. Your ads might be on a spoofed website already, and you won’t know until it’s too late.
Different Types of Website Spoofing
The easiest way to spoof a website is by using a domain URL disguised to look like the URL for the real site. There’s a couple of ways this can be done:
Homograph Attack
A homograph attack uses letters from different languages and Unicode characters that are almost indistinguishable from American Standard Code for Information Interchange (ASCII), the most common character encoding format for text data in computers and on the internet.

If they weren’t side-by-side, could you tell the difference? These alternative characters are used to create ‘homographs’ – phrases (or in this context, domain names) that look almost identical, but aren’t.
While browsers like Chrome and Firefox are equipped to identify when characters from multiple languages are used in a domain name, fraudsters can get round this by using domain names made entirely from one language’s Unicode characters, chosen to resemble ASCII characters.
Typosquatting
A similar approach to a homograph attack, this uses a typographical error to give a domain name that’s nearly the same as the genuine site, e.g. Amazon might be misspelled Amaz0n.
Link Cloaking
Also known as link masking, this technique allows a different domain URL to be shown to those viewing your site.
While there are a couple of legitimate reasons to do this (link cloaking is a common technique amongst affiliate marketers who don’t want to spook visitors with an overly long and complex tracking URL), it’s also a favorite among cyber criminals for the exact same reason.
It’s not just about fake URLs – there’s plenty of other ways to spoof a website. More technically accomplished hackers can create fake URL extensions for real domain URLs, then force a redirect to the spoof site. And techniques like cache poisoning and BGP hijacking exploit weaknesses in standard network topologies to divert traffic.
However, this is next-level cybercrime. Most cybercriminals are content to combine fake URL-based website spoofing with other social engineering forms, such as SMS spoofing or email spoofing.
Website Spoofing vs Email Spoofing
Whereas website spoofing requires a fake website to be built, and then uses techniques to disguise the URL and domain name, email spoofing is comparatively easy to carry out.
Email spoofing takes advantage of email’s open and relatively unsecured systems and protocols, and requires only a faked sender address. It’s so easy to do, and so difficult to stamp out, that there’ even email spoofing websites you can visit to set up a spoofed email address as a ‘joke’ (yes, let’s all take a moment to let that sink in.)
Email spoofing also allows hackers to take advantage of company credentials after a larger hack or DDoS attack, infiltrating company email systems to pose as staff members and obtain customer data.
Generally, a spoofed email will either ask the recipient to reply with their personal data, or direct them on to a spoofed website.
Website Spoofing vs Phishing
If spoofing is the bait, phishing is the hook. Convinced by the faked URL or email address, the user is then asked for information.
Typically, the kind of information they’re looking for will be financial information, like credit card details, or passwords.
When used in combination with a spoofed website, phishing attacks will often seek to steal the login credentials that you would use on the genuine version of that site.
In recent years, we’ve also seen the rise of spear phishing – a carefully planned phishing attack targeting a specific individual whose personal data can give high-level access to a high-value asset, such as a bank or a large company. Often requiring several months of research for a single attack, spear phishing attempts have been detected at roughly 35% of organizations worldwide.
Spoof Website Examples
Spoofed websites can be difficult (and dangerous) to hunt down in the wild, and it’s not a good idea to go clicking through your spam email folder unless you’ve got serious cybersecurity skills.
Xudong Zheng, an associate professor at the University of Maine, put together a fascinating experiment and proof of concept, spoofing the Apple website using a homograph attack.
Why Website Spoofing Happens
Website spoofing happens for two main reasons.
1. To mislead visitors looking for a genuine site, and subject them to phishing attacks and malware. As we’ve discussed, spoofed websites can be used to extract valuable personal data such as passwords, financial information and login credentials.
Website spoofing also allows the victim’s computer to be infected with malware, leaving it open to misuse via botnets or malware-based ad fraud like the infamous DrainerBot scheme, which transformed millions of user devices into fake ad publishing platforms, back in 2019.
2. To generate PPC ad publishing revenue. Spoofed websites can also be misused as ad placement sites. Unsuspecting advertisers use platforms such as Google Ads to provide placements for their ads, not realizing that many of the publishing websites are in fact fraudulent spoofed websites.
While careful targeting allows you to review each site where Google places your ads, a well-spoofed website is more than capable of slipping through Google’s security checks and making it onto your recommended placements list.
Is Website Spoofing illegal?
The legality of spoofing has hit the headlines on numerous occasions recently, as parody sites and social media accounts created for comic purposes have been dragged through the courts by indignant businesses and organizations who don’t appreciate being the butt of someone’s joke.
Website spoofing as a form of social engineering is without a doubt against the law, infringing both copyright and data protection legislation as recognized by almost every country in the world. However, the act of spoofing itself isn’t always considered sufficient evidence.
To take a U.S.-based example, only when the hacker has used the stolen information are they considered to be in violation of 18 U.S. Code 1029 – “Fraud and related activity in connection with access devices”
And as always with any form of cybercriminal activity, legal recourse is still a distant dream. Catching and punishing those responsible is almost impossible. Our legal systems continue to play catch up with our increasingly digitized societies.
Website Spoofing and Click Fraud
So far, we’ve been looking at the weapons of social engineering, and how cybercriminals deceive unsuspecting site visitors and advertisers through emails, text, phishing, and website spoofing.
However, for PPC advertisers, the greatest levels of risk occur when website spoofing is combined with click fraud.

And once your PPC ad has been placed on a fake website, the fraudulent publisher can literally help themselves to your advertising budget, charging you directly for every click – once Google has taken its share for facilitating the placement, obviously.
A cybercriminal who’s prepared to go to the lengths of creating a spoofed domain is likely to be siphoning ad budgets on a fairly large scale, to maximize the return on their efforts. If your ads end up on a spoofed website, you can expect that click fraud will use bots to extract as much of your ad spend as possible, whilst disguising the origin and nature of the click traffic that results.
Website Spoofing Prevention
So, what’s the best way to steer clear of these less-than-amusing spoofs?
Internet users are quite well protected from website spoofing by modern browsers with robust security measures, such as Chrome and Safari. It’s still important to remain vigilant to threats originating from other spoofed sources, however, such as emails and text messages.
Be wary of links or email addresses with typos, or unnecessarily long domain names that don’t quite seem right.
And organizations with whom you hold an account are usually very good at observing recognizable standard practices, which makes it much more obvious when you receive a suspicious request, or their communications stray from the usual template.
PPC professionals face an altogether different set of pitfalls and challenges where website spoofing is concerned.
It’s easy to block a fraudulent ad placement, once you’ve identified it – within a few clicks, it can be added to your Google Placement Exclusion list
However, your main issue is detection. You’ll need to carefully examine your analytics to detect sources of Sophisticated Invalid Traffic (SIVT). Without click fraud protection, SIVT probably makes up a fairly substantial proportion of your overall traffic – it can be really hard to review and identify these unwanted visitors.
To detect website spoofing in amongst your SIVT, you’ll need to be on the lookout for;
- Higher than average volumes of traffic from one site, that don’t convert
- High bounce rates from a single site
- Multiple clicks in a very short space of time
- Repeat clicks from one IP address
- Higher than average cart abandonment rates from one site
If you’re consistently seeing one or more of these symptoms from one of your placements, it’s time to amputate.
In the past five years, PPC advertisers have been offered additional protection from spoofed websites and other forms of social engineering by the Ads.Txt. protocol. This programmatic watermark provides proof of legitimacy and blocks a great deal of malicious activity when used correctly.
However, like all ad fraud countermeasures, ads.txt. is far from infallible – in 2019, investigators from the Wall St Journal uncovered a vast proliferation of spoofed websites and botnets that were circumventing ads.txt. protocol, with an estimated fraud cost of more than $80 million.
For PPC advertisers, spoofing is no joke. While Google and other search engines do a pretty good job of protecting their users as they browse the internet, the combination of website spoofing with email and text spoofing means that no one’s completely safe just yet.
And these tech giants are decidedly less discriminating when it comes to protecting PPC advertisers. The situation may have improved due to the advent of measures such as Ads.txt, but your PPC ads (and budget) are still very much at risk.
Website Spoofing: FAQs
What is a spoofed email or website?
A spoofed email or website is an attempt to deceive internet users, using fake addresses and URLs to pretend to be a reputable online company or organization.
How do you prevent website spoofing?
Website spoofing can’t be prevented. You can, however, mitigate the threats they pose.
As an internet user, spoofed websites are relatively easy to avoid, if you’re careful about opening links, texts, and emails that look suspicious. You can also check the SSL certificate by clicking on the padlock in the URL field at the top of your browser.
As a website owner, you can send ‘cease and desist’ notices to either the CMS (e.g. WordPress or Shopify) or the domain registrar. Failing that, contact Google and ask them to de-index the spoof site. If it’s a recurring problem, there are specific software solutions available.
As a PPC advertiser, using an ad fraud protection solution such as ClickGUARD will help you quickly identify and remove low-quality and fraudulent ad placements automatically
How do you spoof a website?
A website can be spoofed by combining a faked or cloaked URL with stolen intellectual property – using the assets of the genuine website such as their logo, graphic design, color scheme, content, or product lists.
Can a spoof website use saved login info?
It’s very difficult (but not impossible) for a spoofed website to extract saved login info from an up-to-date internet browser such as Chrome or Safari, without the user entering at least some of the saved details into the spoofed site.u003cbru003eEven in the event that you accidentally enter the login info, two-step or multi-factor authentication systems will usually prevent any further incursion from the fraudulent site.